When the victimizers become the victims.... RansomHub the victim of a takeover?
Recent searches
Search options
#raas
Medusa Rides Momentum From #Ransomware-as-a-Service Pivot. Shifting to a #RaaS business model has accelerated the group's growth, and targeting critical industries like healthcare, legal, and manufacturing hasn't hurt either.
https://www.darkreading.com/threat-intelligence/medusa-momentum-ransomware-as-a-service-pivot
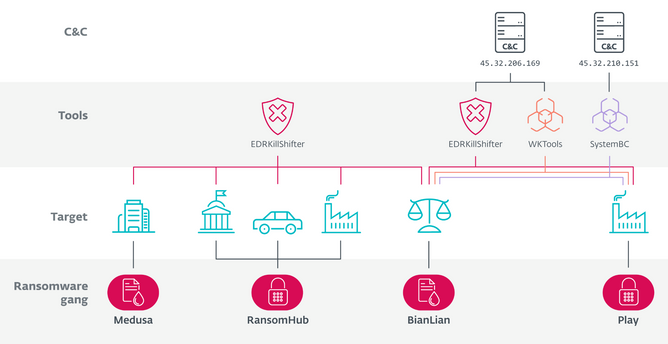
#ESETresearch discovered previously unknown links between the #RansomHub, #Medusa, #BianLian, and #Play ransomware gangs, and leveraged #EDRKillShifter to learn more about RansomHub’s affiliates. @SCrow357 https://www.welivesecurity.com/en/eset-research/shifting-sands-ransomhub-edrkillshifter/
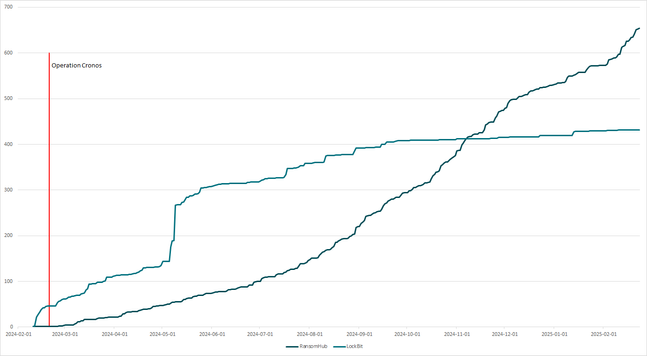
RansomHub emerged in February 2024 and in just three months reached the top of the ransomware ladder, recruiting affiliates from disrupted #LockBit and #BlackCat. Since then, it dominated the ransomware world, showing similar growth as LockBit once did.
Previously linked to North Korea-aligned group #Andariel, Play strictly denies operating as #RaaS. We found its members utilized RansomHub’s EDR killer EDRKillShifter, multiple times during their intrusions, meaning some members likely became RansomHub affiliates.
BianLian focuses on extortion-only attacks and does not publicly recruit new affiliates. Its access to EDRKillShifter suggests a similar approach as Play – having trusted members, who are not limited to working only with them.
Medusa, same as RansomHub, is a typical RaaS gang, actively recruiting new affiliates. Since it is common knowledge that affiliates of such RaaS groups often work for multiple operators, this connection is to be expected.
Our blogpost also emphasizes the growing threat of EDR killers. We observed an increase in the number of such tools, while the set of abused drivers remains quite small. Gangs such as RansomHub and #Embargo offer their killers as part of the affiliate program.
IoCs available on our GitHub: https://github.com/eset/malware-ioc/tree/master/ransomhub
A massive leak of internal chat logs from the notorious Black Basta ransomware-as-a-service (RaaS) group has exposed potential ties to Russian authorities, extensive use of artificial intelligence in its operations and plans for a complete rebranding.

Dragon RaaS | Pro-Russian Hacktivist Group Aims to Build on "The Five Families" Cybercrime Reputation
Dragon RaaS is a ransomware group that emerged in July 2024 as an offshoot of Stormous, part of a larger cybercrime syndicate known as 'The Five Families'. The group markets itself as a sophisticated Ransomware-as-a-Service operation but often conducts defacements and opportunistic attacks rather than large-scale ransomware extortion. Dragon RaaS primarily targets organizations in the US, Israel, UK, France, and Germany, exploiting vulnerabilities in web applications, using brute-force attacks, and leveraging stolen credentials. The group operates two ransomware strains: a Windows-focused encryptor based on StormCry and a PHP webshell. Despite claims of creating a unique ransomware variant, analysis reveals that Dragon RaaS's payloads are slightly modified versions of StormCry.
Pulse ID: 67db2bceaeb33fde1496fef2
Pulse Link: https://otx.alienvault.com/pulse/67db2bceaeb33fde1496fef2
Pulse Author: AlienVault
Created: 2025-03-19 20:40:46
Be advised, this data is unverified and should be considered preliminary. Always do further verification.

Despite global law enforcement actions and source code and decryption key leaks, LockBit is attempting a comeback with the release of LockBit 4.0 Ransomware-as-a-Service (RaaS).
#Ransomware #LockBit #RaaS #Cybersecurity #Security #ThreatIntelligence
https://thecyberexpress.com/lockbit-ransomware-comeback-lockbit-4-0/
#Lagebericht: 2024 haben #Ransomware Angriffe erneut zahlreiche Unternehmen und Kommunen getroffen – mit direkten Auswirkungen auf viele Bürgerinnen und Bürger. Ransomware-as-a-Service #RaaS macht #Verschlüsselungstrojaner zum besonders lukrativen Geschäft. https://bsi.bund.de/Lagebericht
@cloudthethings Sounds like Twitter's new tagline. #RAAS
Analysts had understandably described DISPOSSESSOR as a data broker rather than a ransomware group, but it seems that they have recently teamed up with RADAR and have shifted to a R-a-a-S model while still doing some sales for others.
https://databreaches.net/2024/07/30/radar-and-dispossesor-shift-to-r-a-a-s-model/
De toekomst van humanoïde robots in de industrie: een diepgaande analyse https://www.trendingtech.news/trending-news/2024/06/19326/de-toekomst-van-humano-de-robots-in-de-industrie-een-diepgaande-analyse #humanoïde robots #Agility Robotics #robotica industrie #GXO logistiek #RaaS model #Trending #News #Nieuws
Ransomware: L’attore di minacce “DragonForce” cerca nuovi affiliati per le sue operazioni RaaS
Un recente post su un forum del #darkweb rivela che un gruppo di criminali informatici noto come “#DragonForce” sta attivamente cercando nuovi partner per unirsi alla loro operazione di #Ransomware-as-a-Service (#RaaS).
#redhotcyber #online #it #ai #hacking #innovation #privacy #cybersecurity #technology #engineering #cybercrime #intelligence #intelligenzaartificiale #informationsecurity #ethicalhacking #dataprotection #cybersecurityawareness #cybersecuritytraining #cybersecuritynews #infosecurity
KillSec Annuncia la Nuova Piattaforma Ransomware-as-a-Service (RaaS)
5 Giugno 2024 – #KillSec, un noto gruppo di #hacktivisti, ha annunciato sul loro canale #Telegram il lancio della loro ultima offerta: #KillSec #RaaS (Ransomware-as-a-Service).
#redhotcyber #online #it #ai #hacking #innovation #privacy #cybersecurity #technology #engineering #cybercrime #intelligence #intelligenzaartificiale #informationsecurity #ethicalhacking #dataprotection #cybersecurityawareness #cybersecuritytraining #cybersecuritynews #infosecurity
https://www.redhotcyber.com/post/killsec-annuncia-la-nuova-piattaforma-ransomware-as-a-service-raas/
The Financial Dynamics Behind #Ransomware Attacks
https://securityaffairs.com/164636/cyber-crime/financial-dynamics-ransomware-attacks.html
#securityaffairs #hacking #raas
DATE: June 07, 2024 at 05:54PM
SOURCE: Healthcare Info Security
.
Direct article link at end of text block below.
.
#Qilin #RaaS Group Believed to Be Behind #Synnovis, #NHS #Cyberattack https://t.co/UHBxUY64DK
.
Articles can be found by scrolling down the page at https://www.healthcareinfosecurity.com/ under the title "Latest"
~~~~~~~~~~~~~~~~~~~
Private, vetted email list for mental health professionals: https://www.clinicians-exchange.org
.
Healthcare security & privacy posts not related to IT or infosec are at @HIPAABot . Even so, they mix in some infosec with the legal & regulatory information.
.
#security #healthcare #doctors #itsecurity #hacking #doxxing #psychotherapy #securitynews #psychotherapist #mentalhealth #psychiatry #hospital #socialwork #datasecurity #webbeacons #cookies #HIPAA #privacy #datanalytics #healthcaresecurity #healthitsecurity #patientrecords @infosec #telehealth #netneutrality #socialengineering
Ransomhub: een nieuwe dreiging in de wereld van ransomware https://www.trendingtech.news/trending-news/2024/06/15459/ransomhub-een-nieuwe-dreiging-in-de-wereld-van-ransomware #RansomHub #Ransomware #Cybersecurity #RaaS #Threat Intelligence #Trending #News #Nieuws
FBI vs LockBit: il colpo di scena dopo Operation Chronos! Cosa nasconde il ritorno del leak site?
Sono passati 2 mesi da #Operation #Cronos portata avanti da #FBI, #Europol ed agenzie di altre 10 nazioni che ha scosso il famoso #RaaS Russo. Nelle ultime ore la questione #LockBit è riuscita ad attirare ancora una volta le attenzioni su di se.
#redhotcyber #online #it #ai #hacking #innovation #privacy #cybersecurity #technology #engineering #cybercrime #intelligence #intelligenzaartificiale #informationsecurity #ethicalhacking #dataprotection #cybersecurityawareness #cybersecuritytraining #cybersecuritynews #infosecurity
Thrilled to announce that our paper titled "Supporting Criminal Investigations on the Blockchain: A Temporal Logic-based Approach" accepted at #ITASEC24 is now available online!
De impact van operatie cronos op de raas-industrie en zakelijk risicobeheer https://www.trendingtech.news/trending-news/2024/04/4824/de-impact-van-operatie-cronos-op-de-raas-industrie-en-zakelijk-risicobeheer #Operatie Cronos #RaaS-industrie #LockBit ransomware #cybersecurity #zakelijk risicobeheer #Trending #News #Nieuws
US offers $10 million bounty for info on 'Blackcat' hackers who hit UnitedHealth
The U.S. State Department on Wednesday offered up to $10 million for information on the "Blackcat" ransomware gang who hit the UnitedHealth Group's tech unit and snarled insurance payments across America.
#AlphV #blackcat #RaaS #UnitedHealth #UHG #ChangeHealthcare #Optum #ransomware #malware #security #cybersecurity #Hacking #Hacked
Una azienda italiana con revenue di 6,9 bilion dollar sta per essere attaccata. Scopriamo cosa sono gli IAB
Spesso abbiamo parlato di come funzionano gli #attacchi #ransomware e di come funziona la #piramide del #ransomware as a service (#RaaS), la quale da un ruolo ad ogni team di #hacker #criminali, come visto nell’articolo che cos’è il #ransomware.
#redhotcyber #online #it #web #ai #hacking #privacy #cybersecurity #cybercrime #intelligence #intelligenzaartificiale #informationsecurity #ethicalhacking #dataprotection #cybersecurityawareness #cybersecuritytraining #cybersecuritynews #infosecurity